Removing signatures from Blackberry applications and re-signing them
I was recently exploring the internals of Blackberry COD files and one of the first problems I have got was to remove a signature from the file to be able to modify it and re-apply another signature. One of the primary reasons why I have started all this was my desperate attempt to get some good Blackberry applications working over WiFi only (more articles on this subject will be published soon).
First of all I would like to thank drbolsen for his efforts in reverse-engineering the COD file format. Although I find a bit strange that he publishes the information that is a bit incomplete and his COD decompiler application just does not work, still, great job!
Some background information: As far as I know, Research In Motion has 6 different signatures available: 3, RBB, RRT, RCR, RCC, RCI. First one is to sign the internal RIM code, RCC is a special signer for using the open-key cryptography from Certicom (once I tried to find out how much does it cost and the answer was $xx,xxx dollars!). RCI is an internal signer for Crypto API. 3 other signers are for mortal developers :) Typical applications use RBB, RRT and RCR signers only.
Lets open the COD file in your favorite hex editor. Scroll down to the end of the file. If the application is signed, you will see a section at the end that is easy to recognize (see the picture below):
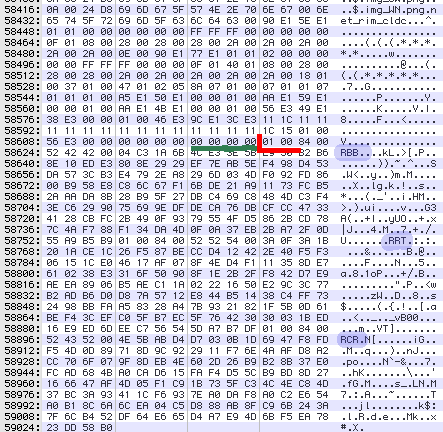
First of all, you will see the signer names (in blue). You may see different number of them - depending on which parts of the API the application is using. If you see RCC there - abandon your hope (unless you have this signature from Certicom). If you see only RBB, RRT or RCR - proceed.
Find the first signer name (i.e. closest to the beginning of the file) and then look towards the beginning of the file for the following hex sequence: 01,00,84,00. This sequence seems to be always aligned to the 4-byte word so it is easy to find (red). Frequently it is preceded with zeros, most likely this is padding. Now all you need to do is to cut off everything starting with 01,00,84,00 and save it to your new unsigned COD file.
Now you can modify the COD file any way you want to. After that you need to re-apply the signature, obviously - your own signature. SignatureTool does not seem to analyze the code in order to figure out which signatures are required for your code. Instead, it relies on the .csl and .cso files generated by the RIM compiler (RAPC). The files are very simple and can be copied from any Blackberry application. So, if your COD file is called "myfile.cod", just create "myfile.cso" as follows:
33000000=RIMAPPSA2 52424200=RIM Blackberry Apps API 52435200=RIM Crypto API - RIM 52434300=RIM Crypto API - Certicom 52434900=RIM Crypto API - Internal
and "myfile.csl" as follows:
52525400=RIM Runtime API 52424200=RIM Blackberry Apps API
That's it, now SignatureTool will gladly sign your modified COD file.
blog comments powered by Disqus